Which of the Following Is Best Used With Vulnerability Assessments
Vulnerability assessments provide information about all the hazards that are likely to occur. A risk assessment typically consists of three primary steps.

Vulnerability Management Services Vulnerability Management Is A Drain On Your Security Team Scans Take Too Long Vulne Vulnerability Management Cyber Security
An ethical hackers assessment sheds light on the flaws that can open doors for malicious attackers.

. Performing a comprehensive risk assessment is the first step in securing your data from threats. Often the most challenging step this requires identifying all of the potential threats. Vulnerability assessment is the process of defining identifying classifying and prioritizing vulnerabilities in systems applications and networks.
Run a port scan. Which of the following best describes the information that risk and hazard vulnerability assessments can provide. Vulnerability identification testing The objective of this step is to draft a comprehensive list of an applications vulnerabilities.
Vulnerability assessments also provide an organization with the necessary knowledge awareness and risk backgrounds to understand and react to threats to its environment. Q18 The type of assessment that is best used to identify classify and prioritize vulnerabilities. The security scanning process consists of four steps.
A vulnerability assessment is the process of defining identifying classifying and prioritizing vulnerabilities in computer systems applications and network infrastructures. A vulnerability assessment is a systematic view of security weaknesses in an information system. Used to identify possible network security issues and can detect vulnerable systems on wired and wireless networks.
A vulnerability assessment is a process so complicated that it often requires a comprehensive approach. It evaluates if the system is susceptible to any known vulnerabilities assigns severity levels and provides recommendations on how to best mitigate moving forward. This assessment assists users in detecting vulnerabilities in servers network host or workstations.
Vulnerability assessment In a world where so much private information is stored and transferred digitally it is essential to proactively discover weaknesses. Testing analysis assessment and remediation. It provides an organization with the needed visibility into the risks that exist concerning external threats designed to take advantage of vulnerabilities.
Which of the following is best used with vulnerability assessments. Measurement of a communitys response capabilities D. 2017 saw a record number of security vulnerabilities with more than 16000 vulnerabilities reported by the end of Q3That is more than in all of 2016 combined.
Used to locate and identify. At a tactical level the vulnerability assessment process can help. How to Conduct a Risk Assessment and Vulnerability Assessment.
Vulnerability appraisal determine current weaknesses in protecting assets use vulnerability assessment tools. Vulnerability and Risk Assessment DRAFT. Are you in dark about the cost of your Mobile App QA.
Grey Box Testing Black Box Testing White Box Testing. This assessment assists users in finding any issues related to database security. Prescribed response actions for each hazard identified in the analysis B.
Risk assessment estimate impact of vulnerability on org calculate risk likelihood and impact of risk. Vulnerability analysis also known as vulnerability assessment is a process that defines identifies and classifies the security holes in a computer network or communications infrastructure. Which type of vulnerability assessments software can check for weak passwords on the network.
There are several types of vulnerability assessment. Detailed and accurate data that can be used for damage assessment documentation C. Of the following which is the best way for a person to find out what security holes exist on the network.
Threat identification classify threats by category design attack tree. Tripwire IP360 is the worlds foremost vulnerability assessment solution that is used by various agencies and enterprises to administrate their security risks. The following best describes the difference between a risk assessment and a vulnerability assessmentRisk assessments consider how each potential hazard will affect critical infrastructure and key resources.
There are several types of assessments that are available but the goal should. Try our mobile app testing calculator. Such assessments assist users in protecting the hosts like servers from attacks if they are not properly tested.
While some organizations are addressing these application security risks quickly others are failing to do so. Asset Identification inventory the assets determine assets relative value. Using the open standards tripwire IP360 enables the integration of risk management and vulnerability into multiple processes of the business.
This would mean that a multiple sub-assessments are to be executed each of which spanning different areas within the evaluated organizations IT system in order the final analysis to be exhaustive enough to produce meaningful results.

5 Best Security Testing Tools Of 2020 Detox In 2020 Security Cyber Security Vulnerability

Cyber Security Vulnerability Assessment Tools Cyber Security Awareness Vulnerability Cyber Security
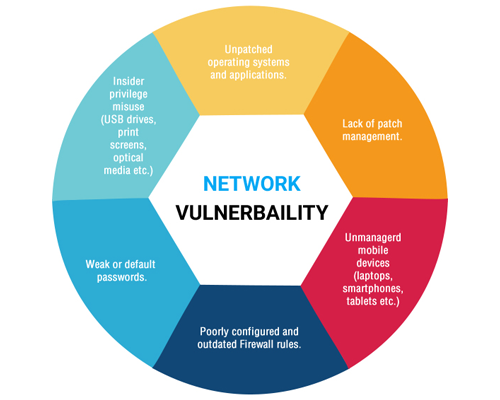
What Is Network Vulnerability Vulnerability Assessment Report
No comments for "Which of the Following Is Best Used With Vulnerability Assessments"
Post a Comment